Archive for the ‘OSINT’ Category
Dickson Yeo: International Man of Mystery *giggle*
I recently went on Blogs of War: Covert Contact and talked with John about online OPSEC and social media. In the process of prepping for the podcast, I went and looked up the stories about LinkedIN being used as a means for Chinese espionage. I had often written about this in the past, and in fact had specifically talked about LinkedIN and how much people over share there. Well, I was given a small surprise when I did, It turns out ‘Dickson Yeo‘, the guy arrested by the feds recently, was someone on my LinkedIN. I remember him as being someone I held at arms length and thought that this account was probably a cutout. Turns out I was right. Full disclosure, he messaged me a few times about posts I had made here and complimented me, but, like I said, and many of you who know me personally, I am not so much a cuddly guy, so he went on his way. Of course later on I was banned from LinkedIN anyway (no I still don’t know why, they would not tell me) so, yeah…. You can hear more on the story and on LinkedIN and our oversharing here on;
Blogs of War Covert Contact: Avoiding Your Own October Surprise
~K
Bellingcat: OSINT Playing Games Where People Tend To Get Burned and Dead
Recently there has been a lot of hubbub about Bellingcat pivoting from tracking military movements and downed planes to exposing GRU operatives who have carried out poisoning operations in the UK. Personally I have watched with a mix of trepidation and angst over what they have been doing recently with the liquidators they have fingered for the Skripal poisonings. I have mixed feelings on all this because while I think they may in fact be right, they could also be being used by their “sources” in Russia as well as possibly be used in future to their detriment by Russia and other nation state services for disinformation operations. Even worse, this group and their OSINT could in fact get in the way of real operations by those same services of friendly nations and could endanger themselves if not others in the field by dropping these bits of intel.
OSINT is a new flavor of the day in the information security world but it has been a long standing practice in certain circles in the other community. The difference here is that the OSINT carried out before was by trained individuals within the intelligence community and not put out for general consumption for the world at large. Today, we have Bellingcat dropping all kinds of data that may or may not be correct that is messing directly with operations by a rogue nation (Russia) and a dictator (Putin) that has no compunction about just killing off the people who oppose him enough to cause him heartburn. This is the big difference here and I just want Bellingcat to take that into account as they do what they seem to be doing with regard to GRU ops. As far as I know, the people who work for Bellingcat are not former intel community, maybe there are some, someone can let me know, but you have to consider that the majority of the people there are not spooks and might be out of their depth in this regard.
Additionally, I would like to reiterate that these discoveries could be actually disinformation provided to you all by services like the SVR to hurt the GRU too. In the world of espionage you are forced to live in the wilderness of mirrors kids. Intelligence analysis is a real art and I am just not so sure your carrying it out completely with these dumps on the GRU carefully considering that fact. Just please consider that you are being played now and if not now, you will be in the future to your detriment by nation state actors for their own goals. That said, please take everything some group gives you so handily, even if the data is in fact correct, as a possible dangle or disinformation operation before you just dump it to the BBC.
Lastly, let me just say again in rather plain language, playing this game can get you dead. Russia is at a point with Putin that they just don’t give a fuck and if you are in their way, and enough of a problem, they will destroy you or kill you. Just look at Sergei and his daughter! Or for that matter, look at Anna Politkovskaya, Alexander Litvinenko, and more than a few other impediments that Putin got rid of. It may not happen now, but I can assure you if you piss them off too much, you will get their unwanted attention.
Just a caution….
Oh, and while I am talking about deaths, it seems that a relative of one of the assassins has been perhaps made missing or killed in Russia as well. So, you all have to consider the possibilities of your hubris in what you do in the form of innocent collateral damage to others.
Just sayin…
K.
About That Manafort Leak…

Paul Manafort, campaign worker for Donald Trump, president and chief executive of Trump Organization Inc. and 2016 Republican presidential candidate, not pictured, speaks with the press during an election night event in New York, U.S., on Tuesday, April 19, 2016. Trump, the billionaire real-estate mogul, got a major boost in his quest to secure the Republican nomination with a majority of delegates but could not eliminate the possibility of a contested convention. Photographer: Victor J. Blue/Bloomberg via Getty Images
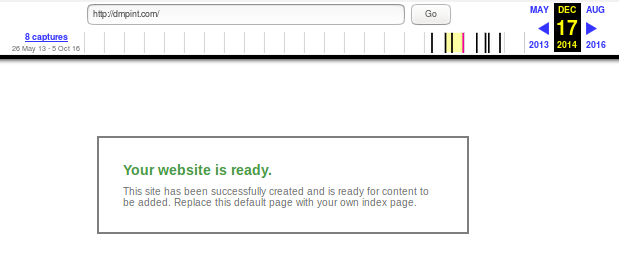
So yeah, I posted a story last week about how a dump of data in the darknet seemed to be in fact Paul Manaforts daughter’s iPhone. It seems that this story was just too good to lose for Politico and the unscrupulous reporter there lifted not only my story but also my images! (yes the hashes match, he just saved them local and re-named them) Politico has done nothing to remedy this and they are churnalists of the worst kind, but they did at least call some people in the Manafort court to see if they would admit to the hack and they did. I could have told them that the hack was real because there was more that I did not post on the blog last time. The fact of the matter is that in the dump there was also a SQL dbase that I got hold of, and in that dump there’s one little interesting factoid. Paul Manafort has an email address that seems to be on a personal domain that isn’t really known about. In the dump connecting with his daughter is a personal iPhone for Paul and in that connection via text is his email address (pmanafort@dmpint.com) when you look up this domain you can see it is one of a few that belong to the Manafort family but registered by another party; one Todd Hankins. Now it seems to me that in an era of “BUT HER EMAILS” this factoid might be of interest to say, I dunno, the IC that he has this and his email is being sent to and from this cutout domain.
Now the domain has never had a site on it and as far as I can see with the limited looking I have done this domain has been kept kinda on the downlow as the Manafort name is not on it like the others. The ONLY thing connecting it to Paul now is the email address and the fact that Todd there set it up for him in 2010. I personally find that interesting… You? I have passed this little tidbit to the right people but now I am going to go wide with it… One wonders as to what emails might lay within that pesky little email system at dmpint.com
Let the FISA WARRANTS FLY!
K.
PS!!!
Google that domain and see what you get… It comes up all Ukraine travel sites… What does Google know hmmmmm?
CYB3RC: The Cyber Caliphate, Newsweek, and DCITA
The Cyber Caliphate Hacks Newsweek and DCITA:
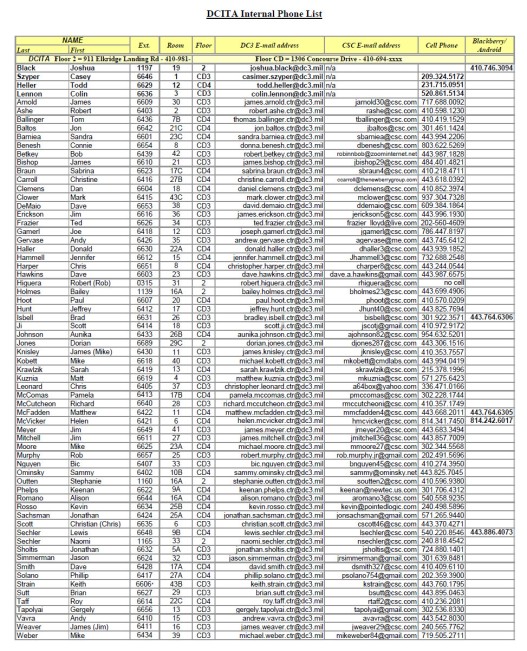
Since the hack on the Pentagon’s CENTCOM Twitter feed and the dropping of dox from someone’s email/phone/machine the so called “CyberCaliphate” had been looking for another target and it seems that they did find a couple in the Newsweek Twitter feed and someone at DCITA (DC3) Defense Base group. On February 10th the Newsweek twitter feed began posting data from another hacked account within the military, albeit the Defense Base side of the house, that showed the Caliphate had culled FOUO data from the DCITA. The documents dumped in screen shot form show internal rosters of phone numbers, some org charts, and other mostly uninteresting documents that are not super secret though sensitive enough to be problematic.
DOCUMENTS LEAKED
PS.. Dear feds, please don’t give me 10 years and a RICO conviction for just posting shit that is already in the open and is FOUO to start ok? *derp*
By problematic I mean that there are some tidbits in there like phone numbers and the types of jobs that these guys hold as well as who they work for, like the guy from the NSA who is signed up for classes. More at issue for me though is that if you look at the email addresses used you see that some of these guys are using YAHOO and GMAIL as their point of contacts! Why is this a problem? Well, because this is supposed to be a group tasked with the security of defense base companies like Pratt & Whitney, Lockheed, and others. Using GMAIL or YAHOO as their primary contact, hell, even a secondary places the information they hold potentially at risk from hacking… Like their shit being stolen and posted on a newly created website and a twitter feed right? This is TERRIBLE OPSEC and COMSEC kids!
The Attribution Games Begin:
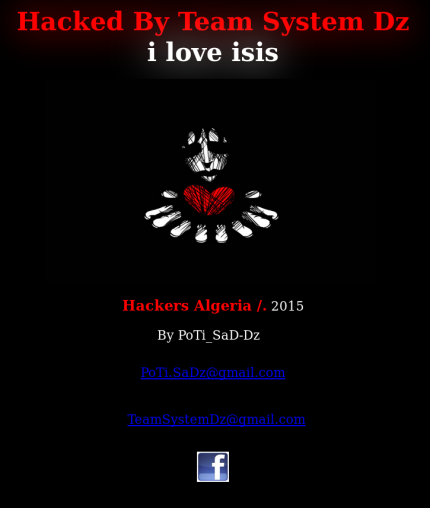
Overall the data is mostly uninteresting as these things go. What is interesting though to me is the kerfuffle that Caliphate is causing and now the crazy attribution game that is going on out there trying to pin these hacks on someone. Originally when the first hack and dump happened the first person that everyone started pointing their collective fingers at was Junaid Hussain ( @AbuHussainIS ) but he actually denied being involved while laughing about the whole thing. Could Juny have something to do with it? Maybe, but he is in Syria and seems to have his own problems lately just trying to keep a twitter feed up. With this second hack and dump though another ersatz attribution wonk claimed that in fact the hacker in question was in fact an Algerian hacker going by the moniker PoTi-SaDz This reporter *cough* made some bold claims but provides no other proof than there is a commonality between the words on defacements made by the Team System DZ crew.
This guys contention is that because the imagery is similar in some of their defacements and the use of :”i Love ISIS” as a slogan clinches it that PoTi SaDz is the infamous Caliphate hacker. Well Matt, I have some other thoughts on that and you should pay attention. First off, please present a little more proof before you play the attribution game. Do you have a source? A snitch? Something other than some poor assumptions to make these claims? Let me give you some for instances here to consider after looking at these guys.
- You claim that they stopped defacing in 2014 and that is incorrect (see screen shot below)
- Have you seen the English used by these guys? It is broken and bespeaks someone who does not really speak it. Now go look at cyb3rc.com and tell me that isn’t a fluent speaker
- PoTi-SaDz M.O. so far has only been defacements and shows no other skill sets to speak of in hacking other systems that might dump these kinds of files
- Hahahaha funny thing.. PoTi calls ISIS alternately Da3sh hahaha Hey Matt, go read up on the word daesh and how ISIS hates that shit
- Nothing on the Caliphate’s posts shows any of these confusions, this person(s) knows about ISIS and is at least on the face of it making a good show of being a supporter without the cluelessness of PoTi
SCREEN SHOTS
So once again, let’s not worry about who did the hacking! Instead let’s focus on how the hack happened in the first place! How did DCITA get powned in the first place? The hack so far looks to be low level, maybe someone’s email or a box that was insecure at the end user level who likely had stuff where they shouldn’t. The whole problem here is that everyone is all up in arms about CENTCOM’s and now DCITA’s stuff being hacked (ERMEGERD) by the daeshbags!
*hangs head*
Trust me people, it would be a better use of time trying to figure out how this shit happened to people who should know better than trying to chase down derpy low level hackers like Caliphate. Wake me when Caliphate hacks something important ok? Until then let me go back to important things like Twitter and watching others fiddle while their digital Rome burns to the ground. Meanwhile, PSSSSST DC3, WTF dudes? Stop this shit! You have important data to watch leave Lockheed’s network! Yeah, I remember fondly the JSF data exfil! Those were the days…
K.
Tweeter, Jihadi, Soldier, Spy: OSINT in the Twitter JIHAD
IS and the Propaganda Wars
Since the time that Zarqawi created AQI and got UBL’s approval the latter day ISIL/IS/Daesh group was a rag tag crew of angry guys looking to blow shit up. Post Abu’s passing and with the rise of Abu Baqr, the ISIL/IS/Daesh group has grown not only in numbers but also savvy on messaging and recruiting. Of course some of this has to do with the shifting nature of the region given all the politics and US screw ups since the invasion in 2003 that allowed for the group to coalesce into what we have today running amok in the region. Once the group really gained traction though, and AQ even turned their back on them for being too brutal, the IS became a force to be reckoned with in the area but now they have spread onto the internet as a means of propaganda warfare and recruitment. Much to the United States chagrin they have been all too successful in propagating their message as well as giving fodder to the main stream media to roll out the fear machine and set it to eleven.
Twitter Jihad
Primarily the IS took the model that AQAP had started and learned what AQAP did not. IS is much more capable at propaganda and slick messaging than AQAP ever was. IS has even now started it’s own magazine “Dabiq” which is much like the Inspire magazine but seems to be much more art directed than Inspire was. Now the Daesh has even broken into full blown advertising with small propaganda films that film school students probably look at and swoon over for their slick nature and editing. These things though do not have as much reach without the Twitter Jihad that is going on in tandem and as their medium for dissemination.
Twitter has been the battle ground of late in the war of ideas between IS and the world. Of course the US has decided that either the accounts on Twitter should be banned (or maybe that is just Twitter making that decision?) but it seems that the net effect here is a great game of whack-a-mole while the world burns. The US has frankly been stymied to come up with a good solution to the problem of the propaganda that IS has been using to get the ummah to come to the jihad but recently they decided that trolling might be the answer they need.
Of course what I would call trolling is not what I am seeing out of the Department of State’s account at all. I am seeing reasoned arguments that are aimed at unreasonable individuals or those who may have some mental issues that need addressing. By being logical and refuting the call to this particular type of jihad you are just going to maybe get a lock on the rational individuals. However, Daesh wants only the cream of the crop in the whacknuttery department to join their ranks or to self radicalize and act out their fantasies here in the West. Much like I would assume the attacker from yesterday in Canada did with his shootem up at the capitol.
Frankly, I have no solid answers on how to respond to all of this. I would love to see some plans in action that would stem the tide here and perhaps staunch the flow of propaganda and jihad on Twitter. So far the only thing I can come up with is what you will see below for those who are either interested in watching the great game at a larger scale or perhaps to get inside of it a little more and work towards some asymmetric solutions. Perhaps the likes of Anonymous and others would truly “Troll” these players and drive them to drink, spending more time wasting time setting up accounts than actually placing their crap online.
… Just a thought…
On the other end of the spectrum this will be a little primmer on perhaps how you might use some tools to get closer to these guys. By getting closer I mean more in the HUMINT side of the house because as we are seeing they are learning that their metadata is on the Twitter as well. A recent manual that came out from Daesh instructing the brothers on how to stamp out their metadata and specifically called out the fact that geotags had been a problem. Well, as you can see at the top of this post that yes, this is a problem for them. However, I would posit that unless you are watching them real time somewhere in the bowels of Twitter HQ the latency issue becomes a key factor in whether or not we can send a drone and a hell-fire up their asses.
Clearly they are learning from their mistakes and it seems of late that the Bellingcat is out of the bag here with regard to things like looking near real time at their metadata through their posting of images and tweets from places like Raqqa and elsewhere. It was this manual that prompted the post you are reading now in fact. After looking at all the data and seeing the immensity of the accounts online now that are jihadi related I think that it’s just too much for the government to handle. For that matter I think it is certainly too much for the private companies to handle as well and once you come to that conclusion you then have to think about how well they don’t all talk to each other. In the end there is a morass out there and from all intents and purposes today from what I have seen the government has no idea what to do about it. There’s just too much noise to even get the signal and soft trolling is just pathetic.
Recon
So it comes to this, I have decided that the best way of creating some tension that might cause pain to the Daesh is to give you all a taste of recon and OSINT on the Daesh. There are many tools out there you can work with and certainly there are fools with tools out there but I would like to see some smarter approaches here. So here goes…
Some tools:
- Recon-ng
- Mentionmap
- Maltego
- twiangulate
- twtrland
- EXIF tools (online and off)
- regex.info
- Foca
- A raft of other command line tools in live distro’s for forensics
It’s a toolbox really and you put the right tools in there that you like and do the job. I am sure you all out there have others you like. These are just a few of the ones I use daily for my fun and games. Lately though I have been leveraging Recon-ng for their twitter features and will be expanding even further into the youtubes and other modules that they have for this kind of work. Suffice to say that you can really profile people on Twitter for example with just this tool alone. Below are some of my outputs for you to see.
 Supporter in Raqqa tweeting 10.17.2014Recon-ng of user on Twitter who is a player within Daesh and is in Syria
Supporter in Raqqa tweeting 10.17.2014Recon-ng of user on Twitter who is a player within Daesh and is in Syria
 Another user logging their connections including their DM connections
Another user logging their connections including their DM connections
 A map of a user and who they talk to/mention with frequency as well as hash tags
A map of a user and who they talk to/mention with frequency as well as hash tags
 Supporter in Raqqa tweeting 10.17.2014
Supporter in Raqqa tweeting 10.17.2014
All of this data is pretty easy to get once you have the right tool sets and a good place to start looking. I leveraged a couple of accounts that I knew of (Adam Gadhan and Juni Al Britani) but you can use others. I will say though once you start spidering ou you will see a flood of accounts out there that are like minded. The trick though is to locate all those users in country and who are real players in the Daesh palooza and this is where you have the analysis phase of the game. As I have said in my posts about Threat Intelligence, it’s all about the analysis and product. If you don’t carry out the analysis well it all means nothing.
PS.. if you don’t know the tools go learn. I am not here to teach you how to use them. Buy the ticket… Take the ride.
Analysis
Analysis of the data here is the part of the cycle that takes a human being. Someone who can make connections as well as verify them. Tools are great but there are many fools with tools out there as I said above so if you use the tool but you fail in the analysis then you will give bad data in the form of connections that are incorrect. In the case of the Twitter jihad you have to have some idea of who you are dealing with. Are you in fact dealing with a real player who is in Raqqa or Ramadi or are you dealing with a wannabe in the US? You have to actually look at all the traffic, understand the language, and the psyche to make any real headway here. Just grabbing user names won’t do and it certainly won’t do if you cannot even Google translate a bit of the language to even have an idea of what is going on.
By analysis of the connections and reading the tweets you can then react appropriately by:
- Passively collecting intelligence
- Actively collecting intelligence
- Actively degrading their activities through disinformation operations
- Actively reporting their activities to authorities (thus degrading their capacities through blocks)
I am advocating all of these things now because this is just Twitter. This stuff is public to begin with and as such it is not like they are planning operational details through Twitter. They are instead advertising really and that to me is up for grabs for the common folk on the internet to attack. I am sure some out there will have a hissy about all of this (Flashpoint, lookin at you Evan you dickweed) but I don’t give a crap. This stuff is just polluting the weak minded and any way to stop it in my book is sauce for the gander.
If you are going to do this then you had best learn OSINT and intelligence analysis. If you want to just scrape names and pass them to Twitter to block, fine, but at least give them the real players and not some hapless reporter ok? Do the work, learn the tools and make a difference.
Asymmetric Response
So what I say to you all out there is pick your plan and go with it. Give the daesh a pain in the ass. I know that in the past Anon’s have been threatening all out war on the jihadi’s on Twitter and I have seen a bunch of nothing come of it. Doxing these guys will only work if they are in the US or another country where they can be picked up.I do fully support the idea though that if you are going to do this then you report them to the authorities. Drop the FBI a dump of accts and maybe some of these guys /girls can get picked up before they pull a stunt like we have seen with be-headings to mass shootings.
The governments trolling is not working and it seems that more and more of these accounts keep popping up. I mean hell, Juni’s on his 103’rd acct right?
Derp.
Just do a good job.. No half ass attempts.. And remember.. I am watching you Daeshbags!
K.
JULY 2014 UNIFIED THREAT INTELLIGENCE REPORT
Unified Threat Intelligence Report
July 2014
Executive Summary
Overall the month of July 2014 has been fraught with new malware campaigns against various entities and this has been the trending since approximately 2010. Malware today is the pivot point for attacks and these campaigns are initiated with emails (phishing) as well as other attacks. The Facebook cross site scripting attack that engages the user to go out of their way to compromise themselves is indicative of where the trend is going and shows how important user education is to malware prevention. As the adversaries grow in number and become more sophisticated in their practices (i.e. crimeware taking on more APT like characteristics) and the re-use of domains between actors it is increasingly apparent that the front line is not only technologies like SIEM and AntiVirus, but also the end users themselves.
Additionally, as the activities of nation state actors continue so too do the operations by hacktivists like SEA (Syrian Electronic Army) and countless other individuals and collectives that will use the same tactics and tools as well. Suffice to say that this is not going away soon and in fact will instead increase geometrically as various countries become more wired across the globe and allow for easy access to the net for these activities. This report is a generalist approach to data that has been in the news cycle within the month of July 2014 but deliberately selected to give a melange of stories that should be considered by any CSO, CISO, or others within domains trying to protect their assets. This is not directed data however, and this is an important part of the intelligence cycle that must be taken into account when reporting to executives. Thus I have placed this report in .odt form on this page for you to download and to add data for your own environment to use in enlightening your staff as to your own metrics on attacks and other activities that affect you directly.
Report Highlights:
- One in five businesses have been hit by Advanced Persistent Threats Global Threats
- Anonymous’: OP ISRAEL attacks Israel over Gaza
- Russian malware infiltrated the Nasdaq servers in 2010
- Microsoft seizes 22 NO-IP domains, disrupts cybercriminal and nation state APT malware operations
- A critical Android vulnerability lets malware compromise most devices and apps
- Facebook suffers a “self” XSS Attack that tricks users into exploiting themselves
- A look at the Android FBI Lock Malware (Ransomware)
- ‘Operation Emmental’ A malware campaign targeting banks across Europe
- Goodwill is Investigating a Possible theft of credit card data
- Nigerian 419 email scammers shift to malware and hacking
- Malware hidden in Chinese inventory scanners targeted logistics, shipping firms in the US and other places
- Manic malware Mayhem spreads through Linux and FreeBSD webservers on the internet
- China: The Pirpi phishing attacks on 7/21/2014
- China: Hacking attacks on NRC National Research Council (Canada)
- Syria/SEA (Syrian Electronic Army) spreads false Rumors of Israel nuclear Leak on Twitter
Global Threats:
One in five businesses has been hit by Advanced Persistent Threats:
Summary:
A recent study of polled participants showed that one in five businesses have been hit with APT attacks. This means that nation state actors such as China have attempted and potentially successfully compromised their systems and ex-filtrated data. What follows are some stats from the polling:
- Approximately 92 per cent of respondents believe that the use of a social networking site increases the likelihood of a successful APT attack, which could prove a threat to a large proportion of businesses.
- 88 per cent think that ‘bring your own device’ combines with rooting or jail breaking by the owner make a successful APT attack more likely.
- Over two thirds of people think that it is only a matter of time before their enterprise is targeted.
- However, despite this, the majority of respondents believe that they are prepared to detect, respond to and stop an APT attack.
- The most common technical control used to protect against these are antivirus and anti-malware, which over 90 percent reported using. This was followed by network technologies such as firewalls, then network segregation.
- Under 30 per cent reported using anti-malware controls on mobile devices.
- Around 96 per cent of the respondents are somewhat familiar of what an APT is, which is more than was reported last year.
- They define an APT as an adversary that “possesses sophisticated levels of expertise and significant resources which allow it to create opportunities to achieve its objective by using multiple attack vendors”. This could come in a variety of formats, and some suggest that it is geared towards the aim of political espionage.
- “They often use the same attack vectors that traditional threats leverage, but they also leverage different attack methodologies and have different characteristics than traditional threats,” the report said.
Analysis:
- APT attacks are not arcane and solely targeting Defense Base corporations.
- The general consensus is that everyone will eventually be targeted in some way
- Generally people do not think that they are properly prepared for these attacks
- That social media access is a key to compromise
- AV products are the main defense against APT campaigns but under 30% have AV on mobile assets
While APT activities have been in the news it is still important to note that not everyone knows what an APT is never mind how they operate. Many still do not consider APT a threat because they have the perception that their environments are not of importance to the Chinese and others. This is a misapprehension that must be corrected. There is always the possibility that your environment may be a target for data that you hold or access that you have leading to another target more sought after. It is important that more within the field of security understand how APT works and separate the hype from the reality.
Anonymous’ Offensive against Israel: OP ISRAEL
Summary:
Anonymous announced last month that they would be attacking Israeli systems to protest their attacks in Gaza and the troubles ongoing in the area. This stemmed from the abduction and beating of youths in the area that now have blown up into all out missile wars between Hamas/Palestine and Israel. The hackers managed to deface many government pages as well as leak user names and passwords to systems.
Analysis:
Overall this type of activity is questionable as to its merit for or against war. In the grander scope of things these attacks do not stop the hostilities between parties or ameliorate much else other than the sense of accomplishment on the part of the Anon’s out there taking part in it all.
The flip side of this is that any action against a corporation of government that is successful will lead to financial loss as well as perceptions of vulnerability for said company or government systems. This is the essence of asymmetric warfare.
Russian malware infiltrated the NASDAQ servers
Summary:
In 2010 the NSA, CIA, FBI, and other agencies learned that the NASDAQ Stock Exchange had been hacked by a Russian individual and malware was placed within their core servers. The malware was a form of logic bomb that could potentially stop trading on Wall Street and thus cause a cascade effect in the global economy.
Analysis:
This incursion into the NASDAQ network shows how one actor can potentially have a mass effect on the local (US) and global economy should his attacks have been carried out. The malware was designed to erase data and lock users out of systems. This would have had a detrimental effect not only in downtime but also in confidence in the stock exchange as well as the economy in general. These types of “Supply Chain” and FInancial attacks will be on the uptick in the future as adversaries work toward global implications of their actions as well as Nation State actors like China who foresee these types of attacks as a necessary tool within the 5th domain.
Microsoft seizes 22 NO-IP domains, disrupts cybercriminal and nation state APT malware operations
Summary:
Microsoft moved to take down the NO-IP dynamic Domain system in an effort to short circuit cybercriminal and APT activities. The service allowed for quick and anonymous creation of dynamic domains that these actors would use as command and control servers for malware. This particular takedown affected a great number of malware systems.
From report:
In addition to these, the takedown disrupted many other APT operations, which used NO-IP for their C&C infrastructure. These include:
Turla/Snake/Uroburos, including Epic
Cycldek
HackingTeam RCS customers
Ladyoffice
Analysis:
This takedown shows the ecology of many of the malware campaigns out there today. They tend to use the same C&C infrastructures that Crimeware inhabits and thus at times it can be hard to determine who the actors truly are. In the case of the Flame and MiniFlame servers this action will be taking out a significant amount of APT activity which may in fact be Israeli in origin. As the actors become more adept at their prosecution of warfare in cyberspace so too will the disinformation and psychological warfare capabilities and actions increase. As a means of knocking out large swaths of C&C Microsoft is taking more solid action by taking the systems down as opposed to watching them as others might do. This is an ongoing discussion within the community as to whether it is better to just remove their access rather than watch them and use that information later within intelligence circles.
Crimeware
Facebook “self” XSS Attacks
Summary:
This attack leverages user’s interest in hacking into “anyone’s” Facebook account. The gist of this attack is the task of fooling the user to input code into their browser that will then exploit the end users account and allow access to it by the attacker.
Analysis:
This exploit works on a premise based in social engineering and psychology. Humans have a penchant for wanting to know unknown things or to be slightly “bad” and thus this attack works. By fooling users into exploiting their own accounts this attack falls more within the social engineering area than anything else.
Critical Android vulnerability lets malware compromise most devices and apps
Summary:
The majority of Android devices currently in use contain a vulnerability that allows malware to completely hijack installed apps and their data or even the entire device.
The core problem is that Android fails to validate public key infrastructure certificate chains for app digital signatures. According to Google’s documentation, Android applications must be signed in order to be installed on the OS, but the digital certificate used to sign them does not need to be issued by a digital certificate authority.
Analysis:
The analysis of this vulnerability is that no system or hardware should be considered to be absolutely “secure” The reason for this is not only that there may be inherent flaws in the systems creation and upkeep but also from end user abuses or misconfiguration.
Secondarily, if you run a BYOD program then Android may be more vulnerable to attack than you may have thought previously. Even with software means to protect your data the system itself could be compromised due to the way it was created.
Android FBI Lock Malware: FIBLOCK-A
Summary:
A new ransomeware scam has been found in the wild by Sophos. This malware masquerades as a FLASH player update/application which then encrypts your phone and ransoms you with the picture shown above. Once you click proceed, the system then presents you with a way to pay a “fine” (see below)
Analysis:
This malware is tricky in that it ostensibly offers something that Android does not have now (i.e. access to Flash) so this tricks many people into installing it in the first place. The malware then takes over the phone and is hard to get rid of.
The final analysis though is that these types of malware and extortion schemes are becoming more commonplace and thus end users should be more aware of these tactics and how to deal with them. In the case of this malware the payment scheme does not mean that they will be able to rid themselves of the malware.
‘Operation Emmental’ Malware Campaign Targeting Banks Across Europe
Summary:
Operation Emmental attacks are spread using phishing emails which masquerade as being sent from a reputed online retailers. These emails contain malware-infested links which users are prompted to click. If victims click on the link, the malware gets downloaded to users’ computers/mobile devices.
The Emmental malware manipulates the configuration of host systems, and automatically vanishes from the system, which makes it undetectable. The DNS settings of the host computer are manipulated to synchronise with an external server (operated by the cyber-criminals).
Emmental malware then loads rogue SSL root certificates within host systems. These certificates are designed to trust the external server controlled by hackers and thereby eliminate security prompts.
Analysis:
This malware creates in effect, a “Man in the Middle” attack and then tricks users into thinking they have a secure session with their site of choice. This attack is even more dangerous because it cleans up after itself and is hard to detect until it’s too late.
The upshot here is that end users should be aware of how to check links in emails before clicking on them and be aware of phishing attacks through regular security education.
Nigerian 419 Email Scammers Shift to Malware and Hacking
Summary:
It seems that the Nigerians have learned that their tactics are losing ground and they have to move on to bigger and better things. It stands to reason that as things become more point and click and the media gives attention to the big losses by malware at large corporations that the 419’ers will get in the game as well. I expect that the phishing emails will have the same tell tale flaws but people will still click on them and infect their machines with malware. All in all this is just another player in a saturated vector that we all need to pay attention to.
Analysis:
Be on the lookout for the usual types of emails but instead of asking for someone to wire something those will instead be links to malware. As these guys get more savvy we all will need to keep an eye out for their phishing emails. On a threat scale these guys aren’t high just yet.
Malware
Historically the Nigerian scammers have been using emails and phone calls to steal money from unsuspecting people. Recently though they have moved into the world of phishing and hacking using phish emails to send people malware. Once the malware has been installed the 419 scammers are acting just like other criminal actors and stealing personal data and passwords. These they then use to steal money or create fake identities for their own purposes.
Analysis:
The 419 scammers are finally getting into the modern world of malware because people have been catching on to their usual routines as well as spam filters are stopping their emails. The scammers then had to change their tactics in order to continue their work and their revenue streams.
This is a natural evolution really but it shows just how effective these tactics are and how easily they can be picked up by people like these.
Malware hidden in Chinese inventory scanners targeted logistics, shipping firms
Summary:
Financial and business information was stolen from several shipping and logistics firms by sophisticated malware hiding in inventory scanners manufactured by a Chinese company. The supply chain attack, dubbed “Zombie Zero,” was identified by security researchers from TrapX, a cybersecurity firm in San Mateo, California, who wrote about it in a report released Thursday.
TrapX hasn’t named the Chinese manufacturer, but said that the malware was implanted in physical scanners shipped to customers, as well as in the Windows XP Embedded firmware available for download on the manufacturer’s website.
Analysis:
This is what is known as a “supply chain attack” and it means that an attacker has managed to attack your supply chain either by stopping it or changing its capacity in some way. These attacks can be devastating to a company where time and flow of product is essential to the business operations. This also can be seen in the light of supply chains such as military and other chains that could be broken to affect warfare in the favor of an attacker.
Manic malware Mayhem spreads through Linux, FreeBSD web servers
Summary:
Malware dubbed Mayhem is spreading through Linux and FreeBSD web servers, researchers say. The software nasty uses a grab bag of plugins to cause mischief, and infects systems that are not up to date with security patches.
Andrej Kovalev, Konstantin Ostrashkevich and Evgeny Sidorov, who work at Russian internet portal Yandex, discovered the malware targeting *nix servers. They traced transmissions from compromised computers to two command and control (C&C) servers. So far they have found 1,400 machines that have fallen to the code, with potentially thousands more to come.
Analysis:
This malware is novel in a couple of important ways. First off it is on UNIX using a common vulnerability and secondly it is a botnet that is also leveraging those systems infected to compromise other systems. UNIX and Linux are the underpinnings of the internet so if this malware infects systems as rapidly as predicted this could be a real juggernaut.
It is recommended that all UNIX systems facing the internet should be looked at and assessed for the vulnerability that allows for this malware to load and add the systems to the botnet.
APT Activities
China: Pirpi/Gothic Panda Phishing Attack 7/21/2014
Summary:
A phishing attack was launched on 7/21/2014 that leveraged a new 0day and had a very short window of opportunity. The attack has been dubbed Pirpi or Gothic Panda (by Crowdstrike) and is now over. Detection of the attack was quick and the duration of the emails and the hacking was approximately three days.
Data and Sample Email:
From: XXXXXXXXXXXXXXX
Subject: Outstanding Invoice
Part of the email body:
Our records show that you have an outstanding balance dating back to January. Your January invoice was for $445.00 and we have yet to receive this payment. Please find a copy of the invoice enclosed.
If this amount has already been paid, please disregard this notice,and let us know that in this link. Otherwise, please forward us the amount owed in full by Aguest 1st. As our contract indicates, we begin charging 5% interest for any outstanding balances after 30 days.
Analysis:
Malware C&C Details:
The links led to resources at hazarhaliyikama[.]com. All emails linked to this domain with a pseudo-random URL paths just like the earlier spam runs from late April. Each recipient was given a unique URI. Examples below….
hxxp://web.hazarhaliyikama[.]com/doc/idear.htm?a=XXddddddd
hxxp://web.hazarhaliyikama[.]com/doc/uid.php?num=XXddddddd
hxxp://web.hazarhaliyikama[.]com/doc/solo.cfm?cg=XXddddddd
hxxp://web.hazarhaliyikama[.]com/doc/list.jsp?x=XXddddddd
hxxp://web.hazarhaliyikama[.]com/doc/reference.cfm?i=XXddddddd
hxxp://web.hazarhaliyikama[.]com/doc/pag.html?vv=Xdddddddd
China: Attacks on NRC (Canada)
Summary:
A “highly sophisticated Chinese state-sponsored actor” recently managed to hack into the computer systems at Canada’s National Research Council, according to Canada’s chief information officer, Corinne Charette. The attack was discovered by Communications Security Establishment Canada.
In a statement released Tuesday, Charette, confirmed that while the NRC’s computers operate outside those of the government of Canada as a whole, the council’s IT system has been “isolated” to ensure no other departments are compromised.
Analysis:
Chinese APT (2PLA People’s Liberation Army) has been active for some time now attacking defense base and other companies. However, of late they have changed tactics and added think tanks and other governmental bodies that suit their intelligence needs. In the case of the Canadian NRC (National Research Council) China seems to be looking for intelligence concerning matters of state with regard to Canada. This is an important pivot and shows that no group is beyond the interest of the Chinese state.
Syria/SEA (Syrian Electronic Army) Spreads False Rumors of Israel Nuclear Leak
Summary:
Hacker outfit the Syrian Electronic Army (SEA cracked the Israel’s Defence Forces (IDF) Twitter account where it posted a fake warning of a possible nuclear leak due to rocket strikes.
The group posted under the IDF (@IDFSpokesperson) account of a “possible nuclear leak in the region after two rockets hit [the] Dimona nuclear facility” which triggered a brief panic among some of the account’s 215,000 followers.
The SEA published a screenshot showing it gained access to the IDF’s Hootsuite dashboard, a Twitter client that manages public tweets and private direct messages. Israel’s defense force later apologized for the erroneous and alarmist tweet advising users it was compromised and would “combat terror on all fronts including the cyber dimension”.
Analysis:
The importance of attacks like these is the use of disinformation and the open forum of Twitter. In this case it was a panic after such news (disinfo) was placed on the account’s timeline. However, in another case last year the same actors placed information that the White-house had been attacked and that President Obama had been hurt. Once that news had been placed on the Twitter stream the stock market went down and panic ensued. These types of attacks can be powerful against companies as well and could cause financial and reputational loss. It is thus important to consider social media accounts as needing extra security attention as they can be breached and misused in these ways.
DOWNLOAD-ABLE ODT FILE HERE
APPENDIX A: LINKS
http://business-technology.co.uk/2014/07/one-in-five-have-experienced-an-advanced-persistent-threat/
http://www.tomsguide.com/us/facebook-self-xss,news-19224.html
http://www.nbcnews.com/tech/security/nigerian-419-email-scammers-shift-malware-hacking-n163491
http://www.theregister.co.uk/2014/07/23/ruskie_vxers_change_dns_nuke_malware_in_swiss_bank_raids/
http://nakedsecurity.sophos.com/2014/07/25/android-fbi-lock-malware-how-to-avoid-paying-the-ransom/
http://www.theregister.co.uk/2014/07/18/malware_linux_freebsd_web_servers/
Dropping DOX on APT: aka Free Lessons on OPSEC!
“And gentlemen in England now-a-bed
Shall think themselves accurs’d they were not here,
And hold their manhoods cheap whiles any speaks
That fought with us upon Saint Crispin’s day.”
“Prince Hal” Henry V Act 4 Scene 3 ~William Shakespeare
Stuck in The Middle with APT and YOU:
If you are like me then you too have to look at the feeds from FireEye, Crowdstrike, Mandiant, and others on a daily basis for my job. The job that I speak of includes fighting APT at times and having to keep executives aware of what is going on as well. Lately though, since the drop by Mandiant on the “China problem” (aka CN actors 1-13) there has been a huge uptick in reports that try to do the same thing, i.e. name and shame those attackers as a means to an end. That means to an end I feel 99.999% of the time is to garner attention by the media and to increase market share.
Others may have reasons that are more closely aligned with “America FUCK YEAH!” and may be well intentioned but misguided to my mind. I have seen the gamut of this and I too have played my roll in this as well. I have dox’d players in the Jihad as well as nation state actors (mostly wannabe’s) on this very blog and have watched as a pile of nothing really happened most of the time. These big companies though that sell “Threat Intelligence” seem to really mostly be driven by attention and marketing appeal for their services than nation state concerns in my opinion when they drop dox on B or C level players in the “great game” and sadly I think this is rather useless, well, in the great game that is, not in the bottom line of lining their pockets right? …But I digress…
Let’s face it folks, we are all subject to the great game and we have little to no power in it on the whole. The APT and the nation state will continue their games of thievery and espionage. The companies selling services will ubiquitously use their “insider” knowledge gathered from all of their clients DNS traffic to generate these reports and market them to garner more clients and we, the people at the end of and the beginning of this process will just have to sit by and get played. Sure, if you are running your program right in your environment and you are getting good threat intelligence telemetry at the least, then you can attempt to staunch the exfil flow but really, in the end that flow is after the fact right? The PWN has happened and you are just being reactive. From this though you feel a certain amount of angst right? So when some company drops dox on some third stringer in China you pump your fist in the air and say “FUCK YEAH! GOT YOU!” and feel good right?
Yeah… I have news for you. It doesn’t mean anything. It will not stop it from happening. In fact, the services you just paid for that just shamed Wang Dong just taught him a valuable lesson….
FREE OPSEC LESSONS!:
What Wang and the PLA just learned is that Crowdstrike offers FREE OPSEC TRAINING! If any of you out there believe that this will curb the insatiable Chinese Honey-badger they have another thing coming. While it may feel like a slam dunk it is really just a Pyrrhic victory in a larger war while it is really in fact a marketing coup. The Chinese don’t care and in fact all they will do is re-tool their exploits/ttp’s/C&C’s and learn from their mistakes to become more stealthy. Really, we are training the 3rd string to be better at their job when we drop all this stuff on the net. This is a direct forced reaction to their being outed instead of attempting to just share the data in a more covert manner within the IC community or other more secretive channels where it could be used effectively in my opinion.
So yeah, some PLA kids got a spanking and now they are known entities but really, this will not stop them from doing their job and it certainly will have an effect of changing their operational paradigms to be more subtle and inscrutable. While the marketing goal has been fulfilled I see really little other value in doing this ….unless there is a greater unseen game going on here. Some might imply that there is another dimension here and that may include disinformation or other back channel pressures by the government. In fact it was alluded to by the Crowdstrike folks that the government is fully aware and part of the whole “process” on these. So, is this also a synergistic tool for marketing AND nation state agendas for the US?
Eh… Given my opinion of late of the current Admin and the IC, not so much. Nope, I think in the end I will stick to the opinion that this is nothing more than marketing smoke and magic…
I hope the third stringers appreciate the free OPSEC lessons. I mean gee, the going rate for classes is pretty high.
K.
ASSESSMENT: OSINT On NUCLEAR POWER SYSTEMS
NUCLEAR FACILITIES AND POWER GENERATION:
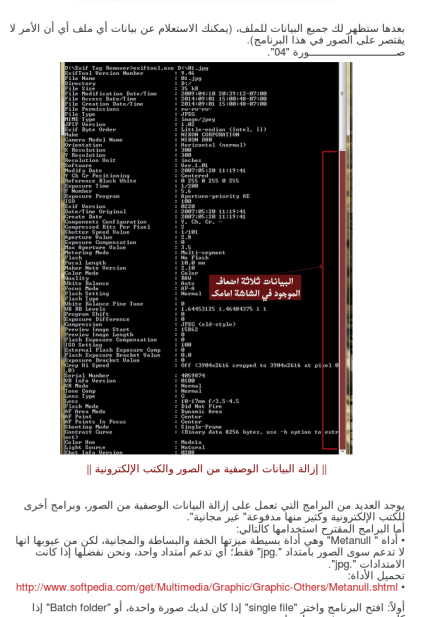
As a second assessment on my power generation and OSINT series I decided to take a look at the security around the nuclear reactors within the US. Currently there is a lot of talk around the grid and the cyber warfare around attacking our power systems but not so much about the nuclear end of that equation. In looking at the bigger picture though, the nuclear facilities should also be on the top of the list for these types of attacks and to assess just how much connectivity there may be to the internet. However, in my assessment I came across much more data surrounding information that not only could help an attacker in attempting to access systems but also data that could help in a successful attack against facilities physically.
Of course the threat assessment today for nuclear facilities per the government where Jihadist terrorism is concerned is that they are not interested in nuclear reactors because they would not be a spectacular event as attacks go. I think this is a stupid mindset or group-think mistake on the part of those who present it as fact. Terror is terror and though a meltdown or a significant release of radiation from a facility would not rival a 9/11 it could cause mass confusion and perhaps result in some deaths. Mostly though, an attack no matter the amount of casualties would so fear and perhaps garner attention that those seeking jihad would desire. In either case, the assessment here will show that perhaps there is data out there that should not be and that perhaps we all should pay a little more attention to what we place on the internet.
OSINT DATA FOUND:
Once again just by using Google searches a lot of ancillary data as well as reports could be found on the NRC site. Whether or not these files are meant to be available online is the question and in most cases perhaps the data is considered to be protected behind HTTPS and within databases that “shouldn’t” be able to be spidered and cached by Google. Some of the data found was in fact in public files that were not marked for security at all while yet still others had been marked FOUO or NOFORN. Some of those documents had in fact been declassified (struck through and enclosures stripped) so they do take pains in most cases to remove data that would be detrimental if it got out. However, there were many files that were available that gave a lot of data to a would be attacker.
Included in the finds online that could just be clicked and downloaded were:
- After Action Reports AAR’s from FEMA and NRC together (table top exercises around nuclear accidents and terrorism drills) that contained remediation plans
- Homeland Security evaluations of sites
- Emails between NRC and companies running facilities
- Emails between government bodies (DHS/NRC/DOE) on sites and systems
In fact there’s a lot of different data to look through and I am not an expert on nuclear facilities or reactors but I am pretty sure that data on their weaknesses and their plans could be of use to an attacker.
 Where current and decomm’d reactors are in the US and how many reactors per
Where current and decomm’d reactors are in the US and how many reactors per
Potential weaknesses in systems
 Electrical systems diagrams for power output and grid
Electrical systems diagrams for power output and grid
 Systems online and their settings
Systems online and their settings
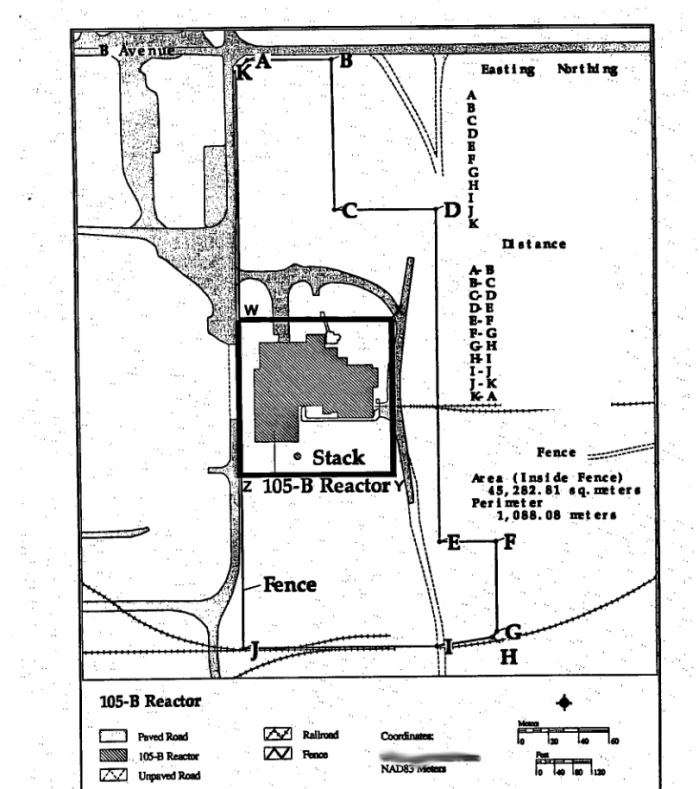
Maps of facilities
 Blueprints of reactor facilities
Blueprints of reactor facilities
 Electrical diagrams of control systems
Electrical diagrams of control systems
 Electrical diagrams of air systems
Electrical diagrams of air systems
ANALYSIS:
My analysis for this OSINT assessment is the following:
- There is enough data out there to be of use to an attacker
- The NRC and other government bodies are leaking data that perhaps should not be
- In some cases in fact NOFORN data was available as well as FOUO online through Google searches
- While most of the physical security testing (red team) data was unavailable online it is still possible to see where vulnerabilities lie with data found
- During this assessment at least no direct data such as passwords to remote SCADA/ICS systems were found in ftp sites (WIN)
It is my suspicion though that with the amounts of emails available a concerted phishing campaign could work very well on the NRC and the companies that run these facilities so one hopes that their OPSEC and technical systems might stop them. Reactors may not be a high value target for the jihadi’s but they aren’t the only ones who would be interested in such vulnerabilities. Given too that there have been a few recent attacks physically on power systems this should be something that we all should care about. We should care about it more as well because these facilities are large producers of megawatts and if taken offline could cause some real problems for the nation or portions thereof.
Another thought that I had was of the concentration of the facilities in the eastern half of the country. A concerted attack to damage them or to cause radiological releases and SCRAM’s could cause large swaths of the country to be under threat of radiation fallout from releases in concert. Of course this would be a very big task and the likelihood is small but it could be something someone would try. With the data available from this sampling one could extrapolate that more searches and a campaign of hacking could gather much more intelligence on the targets. All of this though just points to the fact that there is data out there and that perhaps processes in it’s protection is failing in certain quarters.
K.
So here’s my thing….
VQX HWMVCUSE JQJFASSNTG QV! X HQ JD ISIAVVE!
Face it.. We are all PWND six ways to Sunday
Every frigging day we hear more and more about how the NSA has been emptying our lives of privacy and subverting the laws of this land and others with their machinations. It’s true, and I have been saying as much since the day Mr. Klein came out of his telco closet and talked about how the NARUS system had been plugged into the MAE West back in the day. We are all well and truly fucked if we want any kind of privacy today kids and we all need to just sit back and think about that.
*ponder ponder ponder*
Ok, I have thought about it and I have tried to think of any way to protect myself from the encroachment of the NSA and all the big and little sisters out there. I am absolutely flummoxed to come up with any cogent means to really and truly protect my communications. Short of having access to the NSA supercloud and some cryptographers I don’t think that we will not truly have any privacy anymore. If you place it on the net, or in the air. We have reached in my opinion the very real possibility of the N-Dystopia I have talked about before in the Great Cyber Game post.
As the pundits like Schneier and others groan on and on about how the NSA is doing all of this to us all I have increasingly felt the 5 stages of grief. I had the disbelief (ok not completely as you all know but the scope was incredible at each revelation) Then the anger came and washed over me, waves and waves of it as I saw the breadth and scope of the abuse. Soon though that anger went away and I was then feeling the bargaining phase begin. I started to bargain in my head with ideas that I could in fact create my own privacy with crypto and other OPSEC means. I thought I could just deny the government the data. I soon though began to understand that no matter what I did with the tools out there that it was likely they had already been back door’d. This came to be more than the case once the stories came out around how the NSA had been pressuring all kinds of tech companies to weaken standards or even build full back doors into their products under the guise of “National Security”
Over time the revelations have all lead to the inescapable truth that there is nothing really anyone can do to stop the nation state from mining our communications on a technological level. Once that had fully set in my mind the depression kicked in. Of late I have been more quiet online and more depressed about our current state as well as our future state with regard to surveillance and the cyberwarz. I came to the conclusion that no matter the railing and screaming I might do it would mean nothing to the rapidly approaching cyberpocalypse of our own creation arriving. ….In short, we can’t stop it and thus the last of the five stages for me has set in. I accept that there is nothing I can do, nay, nothing “we” can do to stop this short of a bloody coup on the government at large.
I now luxuriate in my apathy and were I to really care any more I would lose my fucking mind.
OPSEC! OPSEC! OPSEC!
Speaking of losing one’s mind.. Lately people all have been yelling that OPSEC is the only way! One (the gruqq) has been touting this and all kinds of counterintelligence as the panacea for the masses on these issues. Well, why? Why should we all have to be spies to just have a little privacy in our lives huh? I mean it’s one thing to be a shithead and just share every fucking stupid idea you have on FriendFace and Tweeter but really, if you can’t shut yourself up that is your problem right? No, I speak of the every day email to your mom telling her about your health status or maybe your decision to come out etc. Why should the government have the eminent domain digitally to look at all that shit now or later?
If you take measures to protect these transactions and those measures are already compromised by the government why then should you even attempt to protect them with overburdened measures such as OPSEC huh? I mean, really if you are that worried about that shit then go talk to someone personally huh? I know, quite the defeatist attitude I have there huh? The reality is that even though I claim not to be caring about it (re: apathy above) I actually do but I realize that we no longer have privacy even if we try to create it for ourselves with technical means. If the gov wants to see your shit they will make a way to do so without your knowing about it. I fully expect someday that they will just claim eminent domain over the internet completely.
Fuck OPSEC.. I want my government to do the right thing and not try to hide all their skirting of the law by making it classified and sending me an NSL that threatens to put me in jail for breaking the law.
Fuck this shit.
CYBERWARZ
Then we have the CYBERWARZ!! Oh yeah, the gubment, the military, and the private sector all have the CYBERWARZ fever. I cannot tell you how sick of that bullshit I am really. I am tired of all the hype and misdirection. Let me clear this up for you all right here and right now. THERE IS NO CYBERWAR! There is only snake oil and espionage. UNTIL such time as there is a full out kinetic war going on where systems have been destroyed or compromised just before tanks roll in or nukes hit us there is no cyberwar to speak of. There is only TALK OF cyber war.. Well more like masturbatory fantasies by the likes of Beitlich et al in reality. So back the fuck off of this shit mmkay? We do not live in the world of William Gibson and NO you are not Johnny Mnemonic ok!
Sick. And. Tired.
I really feel like that Shatner skit where he tells the Trekkies to get a life…
Awaiting the DERPOCALYPSE
All that is left for us all now is the DERPOCALYPSE. This is the end state of INFOSEC to me. We are all going to be co-opted into the cyberwarz and the privacy wars and none of us have a snowball’s chance in hell of doing anything productive with our lives. Some of us are breaking things because we love it. Others are trying to protect “ALL THE THINGS” from the breakers and the people who take their ideas and technologies and begin breaking all those things. It’s a vicious cycle of derp that really has no end. It’s an ouroboros of fail.
RAGE! RAGE! AGAINST THE DYING OF THE PRIVACY! is a nice sentiment but in reality we have no way to completely stop the juggernaut of the NSA and the government kids. We are all just pawns in a larger geopolitical game and we have to accept this. If we choose not to, and many have, then I suggest you gird your loins for the inevitable kick in the balls that you will receive from the government eventually. The same applies for all those companies out there aiding the government in their quest for the panopticon or the cyberwarz. Money talks and there is so much of it in this industry now that there is little to stop it’s abuse as well.
We are well and truly fucked.
So, if you too are feeling burned out by all of this take heart gentle reader. All you need do is just not care anymore. Come, join me in the pool of acceptance. Would you care for a lotus blossom perhaps? It’s all good once you have accepted the truth that there is nothing you can do and that if you do things that might secure you then you are now more of a target. So, do nothing…
Derp.
K.
Book Review: An Introduction to Cyber-Warfare: A Multidisciplinary Approach
IJPFRH CPAGP EIIL!
CYBER CYBER CYBER!
CYBER CYBER CYBER! or “CRY HAVOC AND LET SLIP THE DIGITAL DOGS OD CYBER WAR!”” is often what you hear from me in a mocking tone as I scan the internet and the news for the usual cyber-douchery. Well this time kids I am actually going to review a book that for once was not full of douchery! Instead it was filled with mostly good information and aimed at people who are not necessarily versed at all in the cyberz. I personally was surprised to find myself thinking that I would approve this for a syllabus (as it has been placed into one by someone I know and asked me to read this and comment)
The book really is a primer on IW (Information Warfare) and Cyber-Warfare (for lack of a better nomenclature for it) which many of you reading my blog might be way below your desired literacy level on the subjects. However, for the novice I would happily recommend that they read the book and then spend more time using ALL of the footnotes to go and read even more on the subject to get a grasp of the complexities here. In fact, I would go as far as to say to all of you out there that IF you are teaching this subject at all then you SHOULD use this book as a starting point.
I would also like to say that I would LOVE to start a kickstarter and get this book into the hands of each and every moron in Congress and the House. I would sit there and MAKE them read it in front of me *surely watching their lips move as they do so* There are too many people in positions of power making stupid decisions about this stuff when they haven’t a single clue. I guess the same could be said about the military folks as well. We have plenty of generals who have no idea either.. That’s just one man’s opinion though.
As we move further and further down the cyber-war road I think that books like this should be mandatory reading for all military personnel as well as college level courses in not only IW/INFOSEC but also political and affairs of state majors as well. We will only continue down this road it seems and it would be best for us all if the next wave of digital natives had a real grasp of the technologies as well as the political, logical, and tactical aspects of “Cyber”
I have broken down the book into rough chapters and subject areas as it is within the book (mostly) It really does cover more of the overall issues of cyber-warfare and methods used (not overly technical) The modus operandi so to speak of the actual events that have taken place are laid out in the book and give you a picture of the evolving of IW to what we see today as “cyber-warfare” I will comment on those sections on what I thought was good and what I thought was derpy of course, I mean would you all have it any other way?
IW (INFORMATION WARFARE) RUSSIA
The authors cover early IW with the Russian saga’s over Georgia and Estonia. There is a lot in there that perhaps even you out there might not know about the specifics of the incidents where Russia is “alleged” to have attacked both countries at different times with different goals and effects. Much of this also touches on the ideas of proxy organizations that may or may not be state run that were a part of the action as well as a good overview of what happened.
In the case of Georgia it went kinetic and this is the first real “cyber-warfare” incident in my mind as cyber-war goes. I say this because in my mind unless there is an actual kinetic portion to the fighting there is no “war” it is instead an “action” or “espionage” so in the case of tanks rolling in on Georgia we have a warfare scenario outright that was in tandem with IW/CW actions.
OUR CHINESE OVERLORDS
Ah Chairman Meow… What book on Cyber would be complete without our friends at the MSS 3rd Directorate huh? Well in the case of this primer it gets it right. It gets across not only that China has been hacking the living shit out of us but also WHY they are doing it! The book gives a base of information (lots of footnotes and links) to ancillary documentation that will explain the nature of Chinese thought on warfare and more to the point Cyber-Warfare. The Chinese have been working this angle (The Thousand Grains of Sand etc) for a long time now and there are more than a few treatises on it for you to read after finishing this book.
The big cases are in there as well as mention of the malware used, goals of the attacks and some of the key players. If you are out to start teaching about Chinese electronic/cyber/IW then this is a good place to start. Not too heavy but it gets the point across to those who are not so up to speed on the politics, the tech, or the stratagems involved.
ANONYMOUS/SEA/LULZSEC
Anonymous, as someone on my Twitter feed was just asking me as I was writing this piece, is also a part of this picture as well. The idea of asymmetric online warfare is really embodied by these groups. The book focuses more on Lulzsec and their 50 days of sailing but it doesn’t go too in depth with the derp. Suffice to say that all of them are indeed important to cyber-warfare as we know it and may in fact be the end model for all cyber-warfare. How so? Well, how better to have plausible denyability than to get a non state group to carry out your dirty war? Hell, for that matter how about just blame them and make it look like one of their ops huh?
Oddly enough just days ago Hammond wrote a piece saying this very thing. He intoned that the FBI via Sabu were manipulating the Anon’s into going after government targets. This is not beyond comprehension especially for places like China as well. So this is something to pay attention to. However, this book really did not take that issue on and I really wished that they had. Perhaps in the next updated edition guys?
THE GRID
OY VEY, the “GRID” this is one of the most derpy subjects usually in the media as well as the books/talks/material on cyber-warfare out there. In this case though I will allow what they wrote stand as a “so so” because they make no real claim to an actual apocalypse. Instead the book talks about the possible scenarios of how one could attack the grid. This book makes no claim that it would work but it is something to think about especially if you have an army of trained squirrels with routers strapped to their backs.
It is my belief that the system is too complex to have a systematic fail of apocalypse proportions and it always has been so. If the book talked about maybe creating a series of EMP devices placed at strategic high volume transformers then I would say they’d be on to something. However, that said, the use of a topological attack model was a good one from a logical perspective. They base most of this off of the Chinese grad students paper back years ago so your mileage may vary. So on this chapter I give it a 40% derp.
WHAT’S MISSING?
All in all I would have liked to have seen more in the political area concerning different countries thought patterns on IW/CW but hey, what can ya do eh? Additionally I think more could have been done on the ideas of offense vs. defense. Today I see a lot of derp around how the US has a GREAT OFFENSIVE CAPABILITY! Which for me and many of you out there I assume, leads me to the logical thought conclusion of “GREAT! We are totally offensive but our defense SUCKS!” So much for CYBER-MAD huh?
I would have also like to have seen more in the way of some game theory involved in the book as well concerning cyber-warfare. Some thought experiments would be helpful to lay out the problems within actually carrying out cyber-war as well as potential outcomes from doing so more along the lines of what I saw in the Global Cyber-Game.
OVERALL TAKE
Well, in the end I think it is a good start point for people to use this in their syllabus for teaching IW/CW today. It is a primer though and I would love to see not only this end up on the list but also the Global Cyber Game as well to round out the ideas here. To me it is more about “should we do this?” as opposed to “LETS FUCKING DO THIS!” as the effects of doing so are not necessarily known. Much of this territory is new and all too much of it is hyped up to the point of utter nonsense. This is the biggest problem we have though, this nonsense level with regard to the leaders of the land not knowing anything about it and then voting on things.
We need a more informed populace as well as government and I think this book would be a good start. So to the person who asked me to review this..
K.