Tweeter, Jihadi, Soldier, Spy: OSINT in the Twitter JIHAD
IS and the Propaganda Wars
Since the time that Zarqawi created AQI and got UBL’s approval the latter day ISIL/IS/Daesh group was a rag tag crew of angry guys looking to blow shit up. Post Abu’s passing and with the rise of Abu Baqr, the ISIL/IS/Daesh group has grown not only in numbers but also savvy on messaging and recruiting. Of course some of this has to do with the shifting nature of the region given all the politics and US screw ups since the invasion in 2003 that allowed for the group to coalesce into what we have today running amok in the region. Once the group really gained traction though, and AQ even turned their back on them for being too brutal, the IS became a force to be reckoned with in the area but now they have spread onto the internet as a means of propaganda warfare and recruitment. Much to the United States chagrin they have been all too successful in propagating their message as well as giving fodder to the main stream media to roll out the fear machine and set it to eleven.
Twitter Jihad
Primarily the IS took the model that AQAP had started and learned what AQAP did not. IS is much more capable at propaganda and slick messaging than AQAP ever was. IS has even now started it’s own magazine “Dabiq” which is much like the Inspire magazine but seems to be much more art directed than Inspire was. Now the Daesh has even broken into full blown advertising with small propaganda films that film school students probably look at and swoon over for their slick nature and editing. These things though do not have as much reach without the Twitter Jihad that is going on in tandem and as their medium for dissemination.
Twitter has been the battle ground of late in the war of ideas between IS and the world. Of course the US has decided that either the accounts on Twitter should be banned (or maybe that is just Twitter making that decision?) but it seems that the net effect here is a great game of whack-a-mole while the world burns. The US has frankly been stymied to come up with a good solution to the problem of the propaganda that IS has been using to get the ummah to come to the jihad but recently they decided that trolling might be the answer they need.
Of course what I would call trolling is not what I am seeing out of the Department of State’s account at all. I am seeing reasoned arguments that are aimed at unreasonable individuals or those who may have some mental issues that need addressing. By being logical and refuting the call to this particular type of jihad you are just going to maybe get a lock on the rational individuals. However, Daesh wants only the cream of the crop in the whacknuttery department to join their ranks or to self radicalize and act out their fantasies here in the West. Much like I would assume the attacker from yesterday in Canada did with his shootem up at the capitol.
Frankly, I have no solid answers on how to respond to all of this. I would love to see some plans in action that would stem the tide here and perhaps staunch the flow of propaganda and jihad on Twitter. So far the only thing I can come up with is what you will see below for those who are either interested in watching the great game at a larger scale or perhaps to get inside of it a little more and work towards some asymmetric solutions. Perhaps the likes of Anonymous and others would truly “Troll” these players and drive them to drink, spending more time wasting time setting up accounts than actually placing their crap online.
… Just a thought…
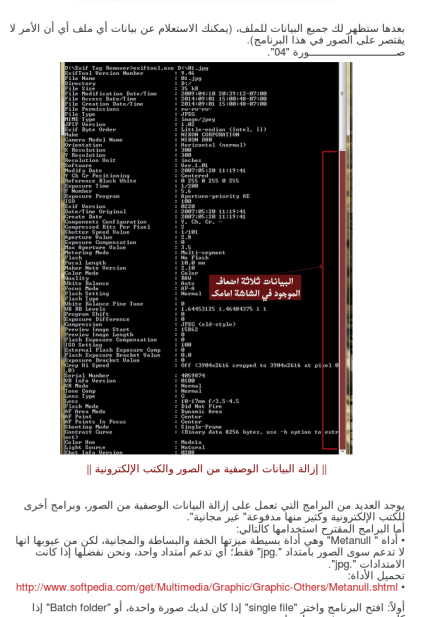
On the other end of the spectrum this will be a little primmer on perhaps how you might use some tools to get closer to these guys. By getting closer I mean more in the HUMINT side of the house because as we are seeing they are learning that their metadata is on the Twitter as well. A recent manual that came out from Daesh instructing the brothers on how to stamp out their metadata and specifically called out the fact that geotags had been a problem. Well, as you can see at the top of this post that yes, this is a problem for them. However, I would posit that unless you are watching them real time somewhere in the bowels of Twitter HQ the latency issue becomes a key factor in whether or not we can send a drone and a hell-fire up their asses.
Clearly they are learning from their mistakes and it seems of late that the Bellingcat is out of the bag here with regard to things like looking near real time at their metadata through their posting of images and tweets from places like Raqqa and elsewhere. It was this manual that prompted the post you are reading now in fact. After looking at all the data and seeing the immensity of the accounts online now that are jihadi related I think that it’s just too much for the government to handle. For that matter I think it is certainly too much for the private companies to handle as well and once you come to that conclusion you then have to think about how well they don’t all talk to each other. In the end there is a morass out there and from all intents and purposes today from what I have seen the government has no idea what to do about it. There’s just too much noise to even get the signal and soft trolling is just pathetic.
Recon
So it comes to this, I have decided that the best way of creating some tension that might cause pain to the Daesh is to give you all a taste of recon and OSINT on the Daesh. There are many tools out there you can work with and certainly there are fools with tools out there but I would like to see some smarter approaches here. So here goes…
Some tools:
- Recon-ng
- Mentionmap
- Maltego
- twiangulate
- twtrland
- EXIF tools (online and off)
- regex.info
- Foca
- A raft of other command line tools in live distro’s for forensics
It’s a toolbox really and you put the right tools in there that you like and do the job. I am sure you all out there have others you like. These are just a few of the ones I use daily for my fun and games. Lately though I have been leveraging Recon-ng for their twitter features and will be expanding even further into the youtubes and other modules that they have for this kind of work. Suffice to say that you can really profile people on Twitter for example with just this tool alone. Below are some of my outputs for you to see.
 Supporter in Raqqa tweeting 10.17.2014Recon-ng of user on Twitter who is a player within Daesh and is in Syria
Supporter in Raqqa tweeting 10.17.2014Recon-ng of user on Twitter who is a player within Daesh and is in Syria
 Another user logging their connections including their DM connections
Another user logging their connections including their DM connections
 A map of a user and who they talk to/mention with frequency as well as hash tags
A map of a user and who they talk to/mention with frequency as well as hash tags
 Supporter in Raqqa tweeting 10.17.2014
Supporter in Raqqa tweeting 10.17.2014
All of this data is pretty easy to get once you have the right tool sets and a good place to start looking. I leveraged a couple of accounts that I knew of (Adam Gadhan and Juni Al Britani) but you can use others. I will say though once you start spidering ou you will see a flood of accounts out there that are like minded. The trick though is to locate all those users in country and who are real players in the Daesh palooza and this is where you have the analysis phase of the game. As I have said in my posts about Threat Intelligence, it’s all about the analysis and product. If you don’t carry out the analysis well it all means nothing.
PS.. if you don’t know the tools go learn. I am not here to teach you how to use them. Buy the ticket… Take the ride.
Analysis
Analysis of the data here is the part of the cycle that takes a human being. Someone who can make connections as well as verify them. Tools are great but there are many fools with tools out there as I said above so if you use the tool but you fail in the analysis then you will give bad data in the form of connections that are incorrect. In the case of the Twitter jihad you have to have some idea of who you are dealing with. Are you in fact dealing with a real player who is in Raqqa or Ramadi or are you dealing with a wannabe in the US? You have to actually look at all the traffic, understand the language, and the psyche to make any real headway here. Just grabbing user names won’t do and it certainly won’t do if you cannot even Google translate a bit of the language to even have an idea of what is going on.
By analysis of the connections and reading the tweets you can then react appropriately by:
- Passively collecting intelligence
- Actively collecting intelligence
- Actively degrading their activities through disinformation operations
- Actively reporting their activities to authorities (thus degrading their capacities through blocks)
I am advocating all of these things now because this is just Twitter. This stuff is public to begin with and as such it is not like they are planning operational details through Twitter. They are instead advertising really and that to me is up for grabs for the common folk on the internet to attack. I am sure some out there will have a hissy about all of this (Flashpoint, lookin at you Evan you dickweed) but I don’t give a crap. This stuff is just polluting the weak minded and any way to stop it in my book is sauce for the gander.
If you are going to do this then you had best learn OSINT and intelligence analysis. If you want to just scrape names and pass them to Twitter to block, fine, but at least give them the real players and not some hapless reporter ok? Do the work, learn the tools and make a difference.
Asymmetric Response
So what I say to you all out there is pick your plan and go with it. Give the daesh a pain in the ass. I know that in the past Anon’s have been threatening all out war on the jihadi’s on Twitter and I have seen a bunch of nothing come of it. Doxing these guys will only work if they are in the US or another country where they can be picked up.I do fully support the idea though that if you are going to do this then you report them to the authorities. Drop the FBI a dump of accts and maybe some of these guys /girls can get picked up before they pull a stunt like we have seen with be-headings to mass shootings.
The governments trolling is not working and it seems that more and more of these accounts keep popping up. I mean hell, Juni’s on his 103’rd acct right?
Derp.
Just do a good job.. No half ass attempts.. And remember.. I am watching you Daeshbags!
K.



[…] this in mind I was intrigued by krypt3ia’s blog […]
Open Source Intelligence gathering and analysis on Twtiter Jihadists | OSINFO
2014/10/26 at 12:35
Reblogged this on Septu Consulting News.
Septu Services
2014/10/26 at 21:11
Just wanted to point out that the above comment pingback:
[…] this in mind I was intrigued by krypt3ia’s blog […]
Was written by me.
http://www.pax-pentest.net/social-media/open-source-intelligence-gathering-and-analysis-on-twtiter-jihadists/
And it looks like http://opensourcesinfo.org/ simply ‘Scoop.it’ in its entirety without attribution.
Now I say this, not because my blog post was anything special, but because I want to make it clear that your writing has inspired a whole new direction and way of thinking for me, and has set me off down a path that stirs within me great excitement & enthusiasm.
Simple as that really.
Stuart
2014/10/28 at 20:47